The Four Phases of LHDN Scam
In April 2022, it was revealed that the personal information of over 22.5 million Malaysians had been leaked online. An increasing number of Malaysians found themselves targeted by fraudsters armed with personal information.
(Versi Bahasa Melayu artikel ini turut disediakan di sini.)
In April 2022, it was revealed that the personal information of over 22.5 million Malaysians had been leaked online. Despite assurances by the Prime Minister's Department that no breaches of official data had transpired, an increasing number of Malaysians found themselves to be targeted by fraudsters armed with personal information. The following month, Senior Minister for Defence Hishammuddin Hussein reassured the public that such data breaches did not pose a threat to national security and that the interior ministry was "more than capable" of addressing the issue. In a bizarre twist of events, however, this week the private chat accounts of Malaysia's prime minister and a cabinet member were compromised. This is the latest in a succession of significant data breaches over the last several months, yet the administration continues to insist there is no need for alarm, providing only a tepid warning to the public to avoid being deceived by hackers.
Through social media, several government agencies have urged the public not to fall for scams by issuing digital pamphlets, posters and social media postings as messaging strategy, yet the problem persists despite their efforts. This is because the problems are threefold:
1. Policymakers failed to recognise that weak policies that apply to online systems are increasingly impacting people offline;
2. The public is being targeted by fraudsters who are capitalising on their lack of understanding of how the government operates; and
3. Bad actors are exploiting the fact that government process is regarded as opaque and difficult to substantiate by many.
To demonstrate these points further, consider the case of @TheVenusDarling. She was recently targeted by a scammer who, armed with her personal information, attempted to swindle her through social engineering.
Prologue: Setting the Stage for Shock and Awe
It began with her receiving a phone call from someone claiming to be an officer of the Inland Revenue Board (LHDN) who said she owed them more than RM50,000 in arrears via a business created under her name, reportedly in Melaka. The caller seemed authoritative and convincing, and even supplied a reference number. After putting her on hold (furnished with hold music, even), the caller connected her to a "police inspector" who ordered her to hang up and first google the local police headquarters number as a "verification" measure. He then called her from the exact same number, with background and police radio sounds audible in the background.
Because of this elaborate spoofing approach, the target is now prepped for the deception.
Phase 1: Dismay
Next, the "inspector" proceeded to "take note" of her statement. He then informed her that he ran a check and found there was an arrest warrant out for her because her ATM card was discovered to be linked to fraudulent activities and money-laundering. The target is now dismayed.
Phase 2: Isolate
The "inspector" assured her that he would get to the bottom of things, and passed the call to a "higher-ranking officer". The latter then began to berate and threaten her if she did not comply. In addition, he instructed her to keep the conversation discreet and to move to a quieter area to ensure the conversation remains private. He then informed her that she needed to standby for him to send over some documents via WhatsApp for her to review.
Phase 3: Overwhelm
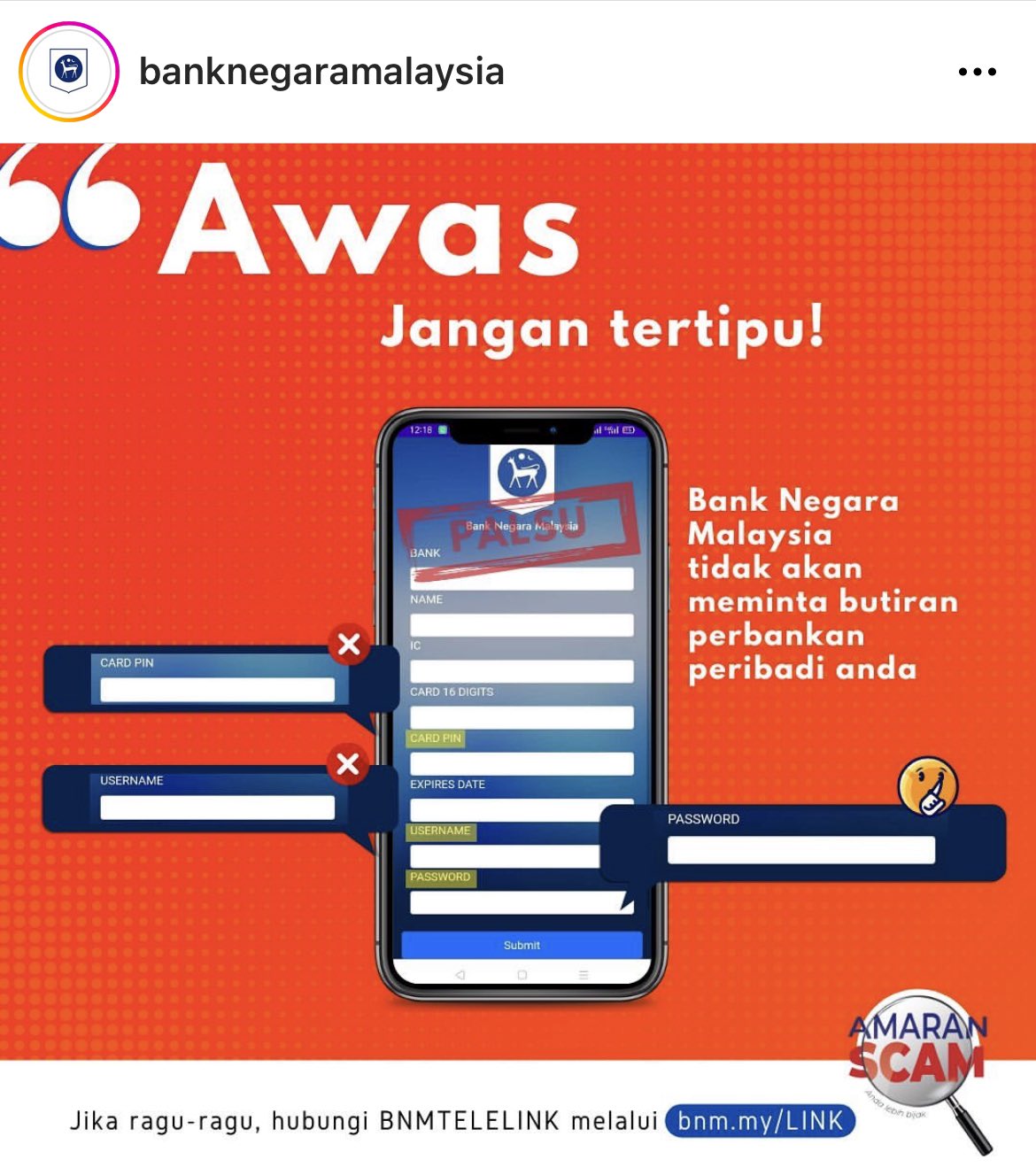
He forwarded her the so-called "warrant" over WhatsApp (see below). With the Royal Malaysia Police emblem, it might seem credible to the untrained eye. The document contained private details such as her legal full name, IC number, home address, phone number, and gender. The target now felt overwhelmed by the avalanche of personal information being exploited against her.

Following this, he directed her to download an app (an .apk file was sent via WhatsApp), ostensibly an official Bank Negara Malaysia (BNM) app, to aid with the "investigation" (see below). She was prepared to enter her PIN when her instincts finally kicked in and she remembered in the nick of time that she was not supposed to share her PIN with anyone. That was when the realisation hit her like a ton of bricks that she was about to be scammed.
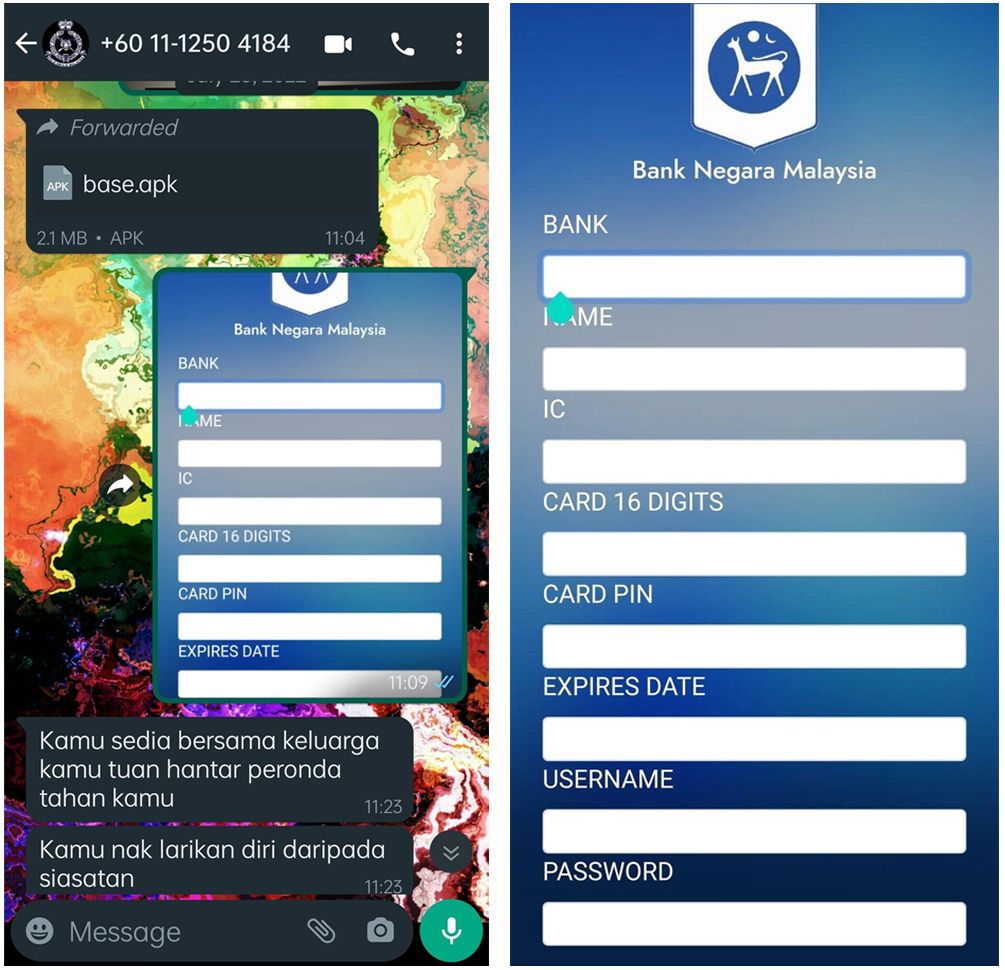
Phase 4: Intimidate
Sensing her hesitation, he began shouting at her as an intimidation tactic to coerce her into giving up her PIN. Luckily, this time, she abruptly ended the call and immediately uninstalled the app.
Unfortunately, in this instance, uninstalling the app is not sufficient. This was when she sought my counsel. Even with the application deleted, we had to assume that the device remained infected with malware. Hitting reset would have been the recommended option, however that would result in data loss - an outcome not many are willing to go for.
Step 1: Log off.
Because we were unable to determine the degree to which her device was compromised, I instructed her to log out of all of her mobile applications and update her passwords on her PC to mitigate further possible intrusions.
Step 2: Surface Sweep
Next, I instructed her to run a sweep. She ran Play Protect, which reported no malicious apps were detected
Step 3: Deep Sweep
Dissatisfied, I directed her to scan using a malware detection tool. She downloaded and ran ESET Mobile Security. The malware was discovered.
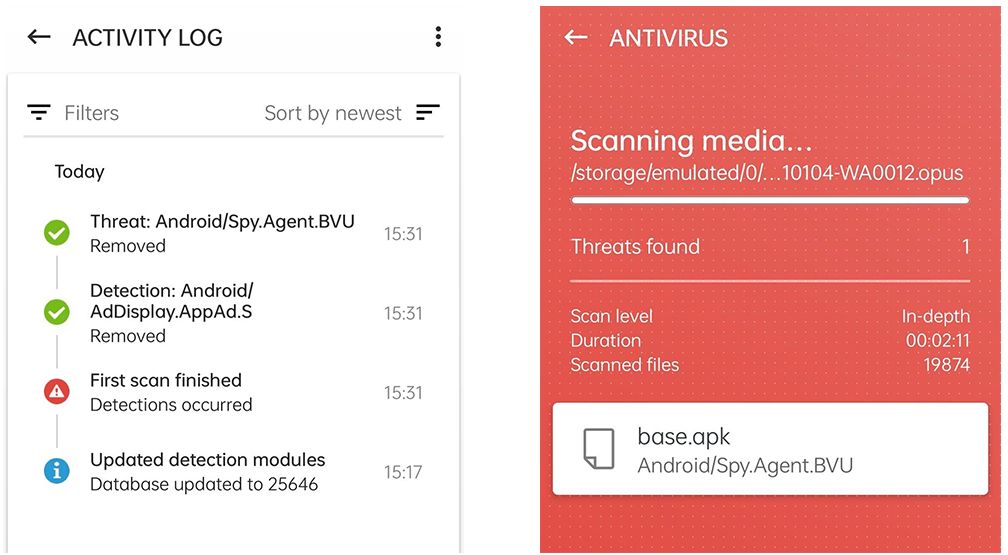
That was not the only intriguing aspect. Like a digital version of The Ring, it was clearly designed to harvest your digital riches. Even though the malware had been on her device for less than five minutes, the infiltration was quite pernicious.
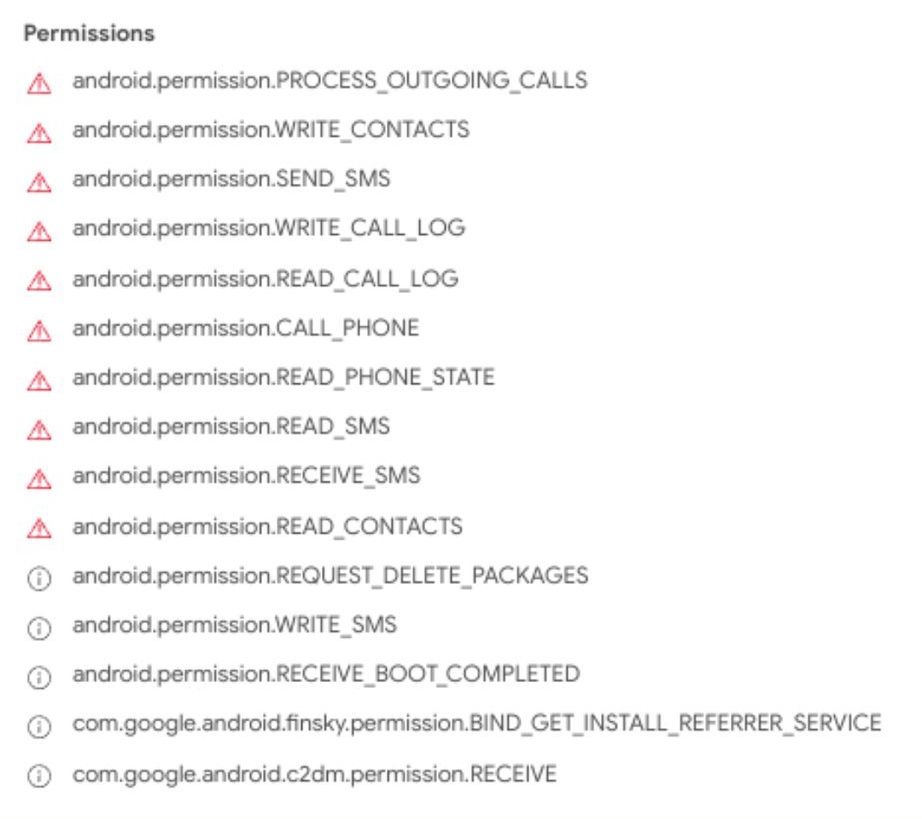
How Did We Get Here?
As soon as @TheDarlingVenus' experience was shared on Twitter, many responses that poured in asserted that the fraud could have been averted from the start had she either hung up on the police impersonators or demanded that they disclose further information, such as badge numbers. Some of them even wanted to know how she could not have known by default that LHDN seldom calls and usually sends out official correspondence through mail. There was also clamouring for such apps to be blocked to prevent further downloads by other potential victims.
This is where it is necessary to dissect the episode and responses to understand why we remain to be besieged. But first, we need to acknowledge that victim-blaming is unproductive. For one thing, victim-blaming justifies high-level apathy. We cannot dispute that bad actors developed these social-engineering techniques because they rely on the public's limited knowledge of government and police procedures, which will continue to serve as a huge security vulnerability. Moreover, this very fact belies assertions that data breaches represent no serious threat to national security, since they have reduced our resilience and increased our susceptibility to financial crimes.
Second, we must recognise that this problem will continue unabated so long as we fail to address it as an institution-wide policy matter. People will continue to be the target of fraudsters as long as they have the means and capability to operate in a target-rich environment that is poorly understood by the very same policymakers who are doing little to combat them. Demanding for the harshest punitive measures is useless because such penalties have failed to demonstrate that they can effectively deter these opportunistic criminals. And thirdly, we must accept that technical solutions are similarly futile, since blackholing IP addresses could have severe and long-lasting consequences for political dissent.
Nonetheless, all is not lost since there is a practical solution. Raising public awareness remains to be the most beneficial and realistic plan of action we could pursue. Even though LHDN and BNM have been actively engaging in social media messaging, the key point from this is that fraudulent activities are happening not because LHDN and BNM are not doing enough to alert the public about the scam; the reality is that this line of effort will always be insufficient. This is simply because large segments of the population continue to be unfamiliar with government processes, which is why these incidents persist. Therefore, the general populace must be properly informed about the government's procedures and standards. And in order to do this, it is vital to enhance the accessibility, clarity, and transparency of information that is already widely available.
Final Thoughts: Target Hardening
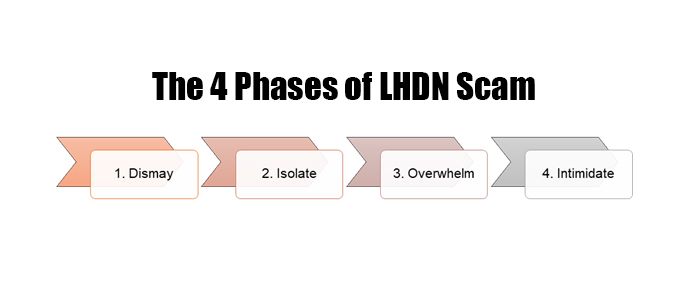
Once you learn the pattern, it becomes somewhat easier to recognise a scam since they are almost always similar. Based on the accounts of a few other victims, the following stages have been identified: 1) Dismay, 2) Isolate, 3) Overwhelm, and 4) Intimidate.
Therefore, it would be in everyone's best interest to familiarise oneself with the MO and learn how to spot a scammer from the very first ring so they can confidently hang up without worrying about a looming police arrest.



